API Authorization
EF API uses fine-grained authorization model based on logical entities and operations. This allows you to control what each API key can do by granting specific permissions related to certain entities (e.g., users, orders) and operations (e.g., READ, WRITE).
Permission Structure
Each endpoint in our API is described by the following elements:
- Entity: The primary resource the endpoint operates on (e.g.,
profile,user,application). - Subentity (optional): A more granular resource the endpoint operates on (e.g.,
applicationunder theprofileentity). - Operation: The action the endpoint performs i.e
READorWRITE
Scope Definition
The scope required for an endpoint is a combination of the above elements and is written in one of the formats:
<entity>:<subentity>:<operation><entity>:<operation>
For example:
profile:application:READ– This scope refers to the permission required to read theapplicationresource under theprofileentity.profile:READ– This scope refers to the permission required to read theprofileresource.
A key can be granted one or more of these scopes to determine the level of access it has to different parts of the API.
Managing API keys and permissions
API keys can be generated from the Admin Console of your application. The Admin Console allows you to manage which permissions are assigned to each API key. Each key can be granted one or more scopes, depending on what level of access you want to provide.
-
Generate API Key: To generate an API key, navigate to
Admin Console->Integration->Eightfold APIand click Generate a new API key button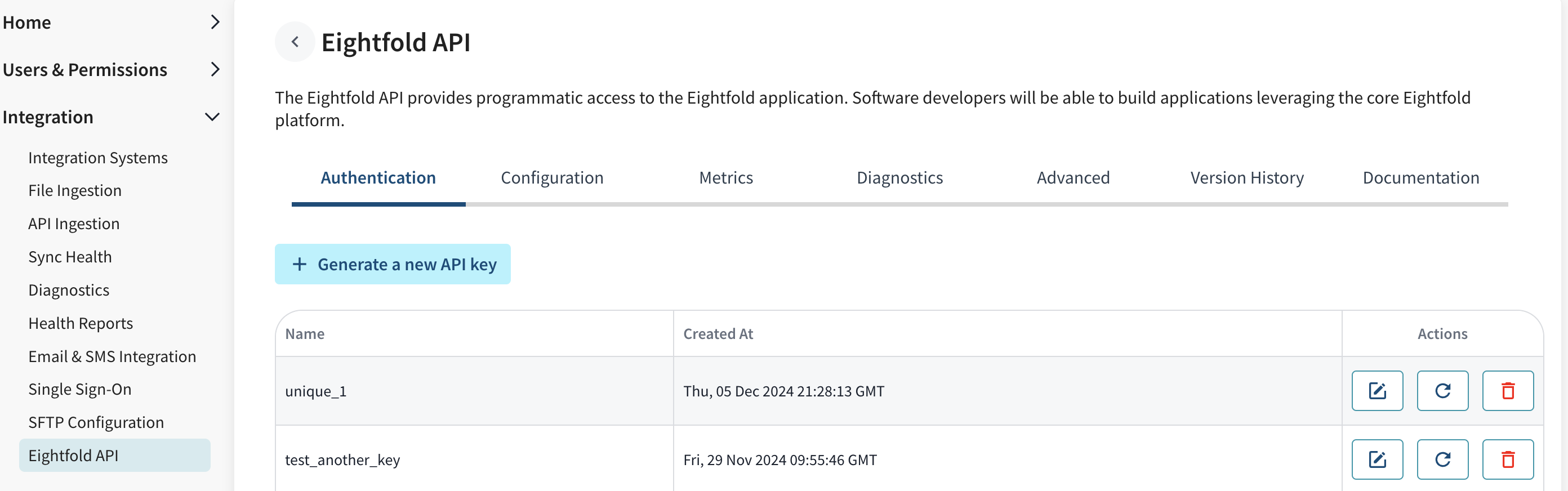
-
Configure Permissions: Each API key can be configured with an Authorization matrix similar to below. Each row corresponds to an entity, with expandable child rows for subentities. The columns, Read and Write, define the operations allowed for each entity or subentity. Checkboxes in the table let you enable or disable these permissions, ensuring precise control over access.
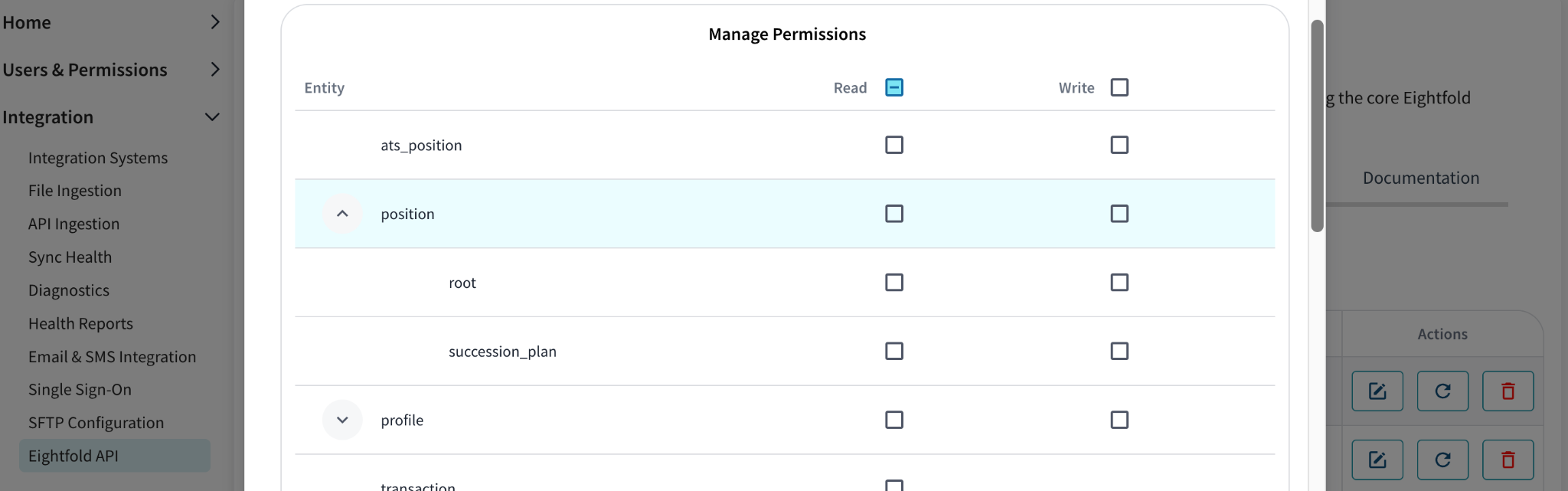
Endpoints Reference and Authorization Scopes
Below is a list of API scopes and their associated permissions:
| Endpoint Summary | Path | Required Scope |
|---|---|---|
| ATS Position Get | /ats-systems//ats-positions/ | ats_position:READ |
| ATS Position Update | /ats-systems//ats-positions/ | ats_position:WRITE |
| ATS Position Patch | /ats-systems//ats-positions/ | ats_position:WRITE |
| ATS Position List | /ats-systems//ats-positions | ats_position:READ |
| ATS Position Create | /ats-systems//ats-positions | ats_position:WRITE |
| Position Get | /positions/ | position:READ |
| Position Update | /positions/ | position:WRITE |
| Position Patch | /positions/ | position:WRITE |
| Position List | /positions | position:READ |
| Position Create | /positions | position:WRITE |
| Position Matched Candidates | /positions//matched-candidates | profile:READ |
| Profile Get | /profiles/ | profile:READ |
| Profile Update | /profiles/ | profile:WRITE |
| Profile Delete | /profiles/ | profile:WRITE |
| Profile List | /profiles | profile:READ |
| Profile Matched Positions | /profiles//matched-positions | position:READ |
| Career Hub Suggest Skills Get | /careerhub/suggest-skills/ | profile:skills:READ |
| Career Hub Career Planner Roles Get | /career-planner//roles/ | profile:role:READ |
| Career Hub Career Planner Roles Patch | /career-planner//roles/ | profile:role:WRITE |
| Career Hub Skill Gap Analysis Get | /career-planner//skills/skill-gap-analysis | profile:role:READ |
| Career Hub Recommended Courses Get | /career-planner//courses/recommended-courses | profile:course:READ |
| Profile Feedback Get | /profile-feedbacks/ | profile:feedback:READ |
| Profile Feedback Batch Fetch | /profile-feedbacks/batch-fetch | profile:feedback:READ |
| Profile Application Get | /profile-applications/ | profile:application:READ |
| Profile Application Batch Fetch | /profile-applications/batch-fetch | profile:application:READ |
| Profile Application List | /profile-applications | profile:application:READ |
| Profile Application Create | /profile-applications | profile:application:WRITE |
| Profile Application Patch | /profile-applications/ | profile:application:WRITE |
| Position Matched Candidates Batch Fetch | /positions//matched-candidates/batch-fetch | profile:READ |
| Profile Batch Fetch | /profiles/batch-fetch | profile:READ |
| Position Batch Fetch | /positions/batch-fetch | position:READ |
| Batch Position Update | /positions/batch-update | position:WRITE |
| Position Delete | /positions/ | position:WRITE |
| ATS Position Delete | /ats-systems//ats-positions/ | ats_position:WRITE |
| User Profile Fetch | /users//profile | user:READ |
| Career Hub Get | /careerhub//profile | profile:READ |
| Career Hub Role Patch | /career-planner//role | profile:role:WRITE |
| Career Hub Skill Patch | /career-planner//skills | profile:role:WRITE |
| Batch Profile Feedback | /profile-feedbacks/batch-fetch | profile:feedback:READ |
| Position Summary | /positions//summary | position:READ |
| Position Skills | /positions//skills | profile:READ |
| User Profile Update | /users//profile | user:WRITE |
| Transaction Get | /transactions/ | transaction:READ |
| Transaction List | /transactions | transaction:READ |
| Batch Transaction Fetch | /transactions/batch-fetch | transaction:READ |
| Job Profile Fetch | /jobs//profiles | profile:READ |
| Job Position Get | /positions//job | position:READ |
| Position Job Fetch | /positions//job | job:READ |
| Candidate Profile Get | /candidates//profile | profile:READ |
| Candidate Profile Update | /candidates//profile | profile:WRITE |
| Candidate Profile List | /candidates | profile:READ |
| Candidate Profile Delete | /candidates//profile | profile:WRITE |
| Role Fetch | /roles/ | role:READ |
| Role List | /roles | role:READ |
| Batch Role Fetch | /roles/batch-fetch | role:READ |
| Role Assign | /roles//assign | role:WRITE |
| Role Revoke | /roles//revoke | role:WRITE |
| Candidate Apply | /candidates//apply | application:WRITE |
| Candidate Status | /candidates//status | application:READ |
| Batch Candidate Apply | /candidates/batch-apply | application:WRITE |
| Profile Skill Update | /profiles//skills | profile:skill:WRITE |
| Candidate Skill Update | /candidates//skills | profile:skill:WRITE |
Note: Ensure that API keys are kept secure and are not exposed in client-side code or logs. Misuse of an API key can result in unauthorized access to sensitive data.
Updated 9 days ago
